Monitor security risks of dependencies into Java project
Check vulnerabilities by using OWASP dependency check
Nowadays, a big part if not the major of an application code comes from dependencies (most often open source). Open source components as others can be subject to vulnerabilities. Once a dependency is added into a project, informations related to this dependency are not always monitored (new version, detected vulnerabilities and so on). In order to provides the most robust and secure application, it will be benefit to track risks related to these dependencies.
The OWASP Dependency Check is an utility that identifies project dependencies and checks if there are any known, publicly disclosed, vulnerabilities. The tool is suitable to analysis dependencies of your Java project and can be easily integrated into your build process since it support Ant, Gradle, Maven and Jenkins. You can also uses it from command line. Nevertheless, best results will be obtain by integrating it into your build process, particularly if dependencies are downloaded because with command line, they will be not downloaded (you need to specify jar files to analyze).
To understand how OWASP Dependency Check works, I use a sample project written in Java and builds with gradle. This projet uses the following dependencies:
|
|
OWASP dependency check gradle plugin
To get the most precise results, the best is to use the Gradle plugin of OWASP Dependency Check. Enable the plugin by adding the following lines into your build.gradle:
|
|
Then check dependencies with the following command line:
|
|
From the sample project, the OWASP Dependency Check tool found 4 vulnerabilities as show into the below screenshots. The report also provide a detailed description of detected problems with a link to the CVE(Common Vulnerabilities and Exposures) from the NVD(National Vulnerabilities Database) website
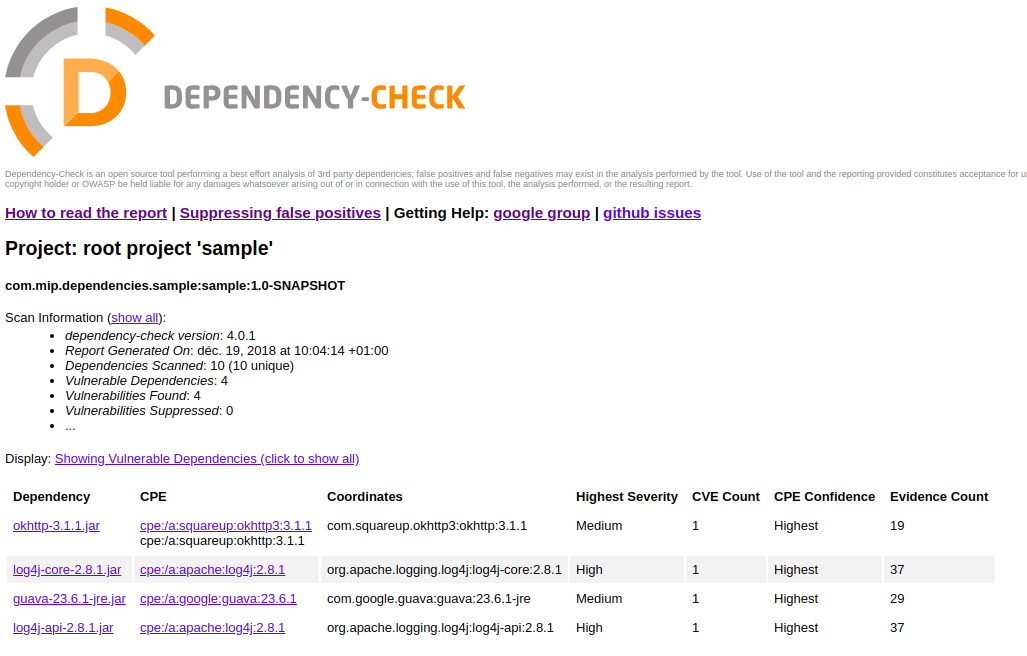
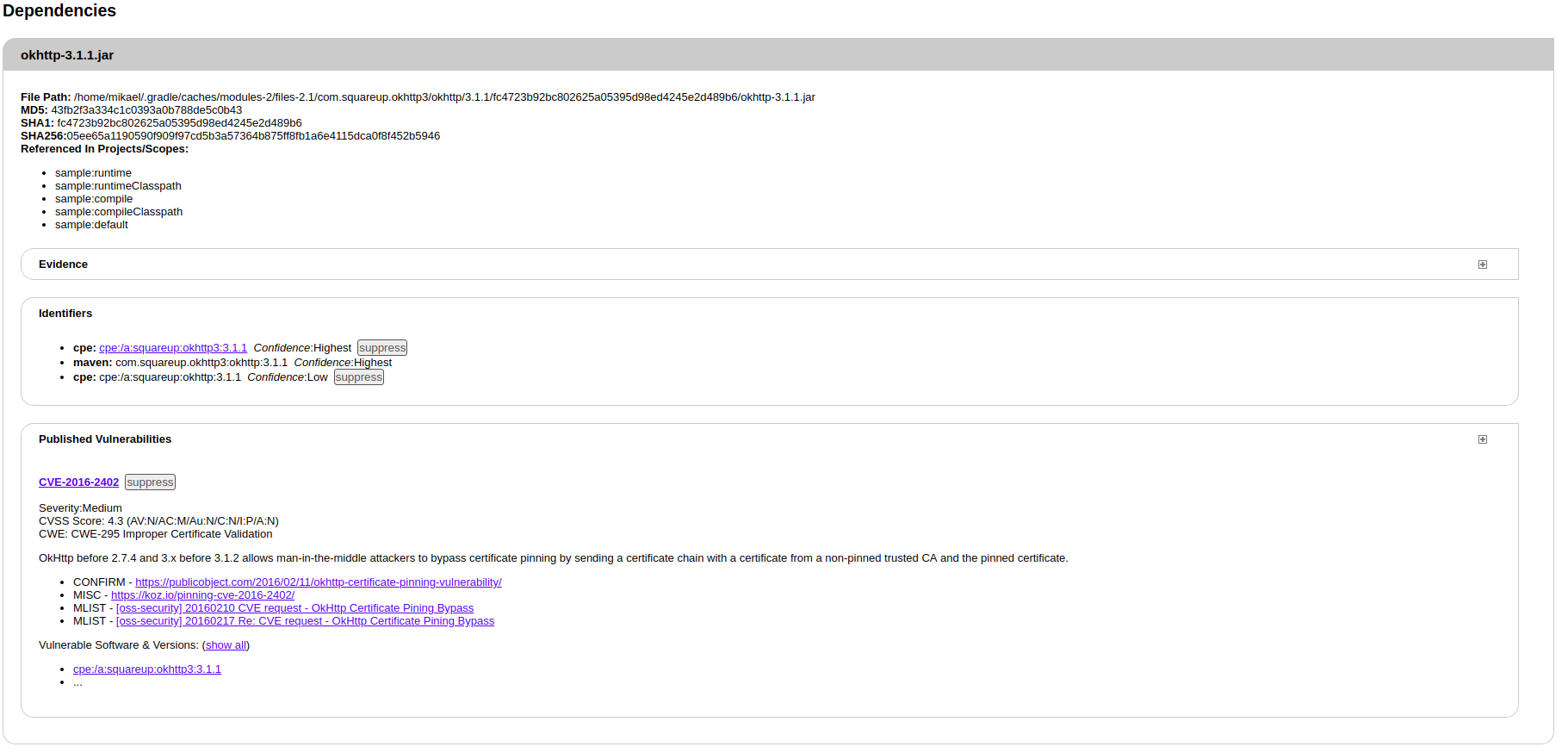
OWASP dependency check jenkins plugin
OWASP Dependency Check tool can also be integrated into Jenkins, one of the leading open-source automation servers. Use it through docker with the following command line:
|
|
If your Jenkins installation is in french and that you prefer to have it in english, install the Locale plugin, then go to Administrer Jenkins/Configurer le système, then into the Locale section and sets default language to en_us and check the box Ignore browser preference and force this language to all users
Create a new Freestyle job project that will build your sample project. In the Source Code Mangement section, set the git repository url of your sample project and specify the branch that you want to checkout, then trigger a manual build to check that all is correct.
Now install the OWASP Dependency Check plugin by going to Manage Jenkins/Manage Plugins, into available plugins select OWASP Dependency-Check and install it without restart.
In order to add dependency check analysis into your build job, go to the project and select Configure, into the Build section, add a build step that will invoke gradle script and set the tasks to dependencyCheckAnalyze. To finish, into the Post-build Actions, add a step to publish dependency check result and keep the default configuration. Results will be published by using the generated XML report.
❗ Do not forget to configure the tool to generate the XML report by adding the following line into your build.gradle
|
|
Once results are published, Jenkins provides you with a detailed results as well as vulnerabilities trend graph allowing you to quickly known the risk states of your project.
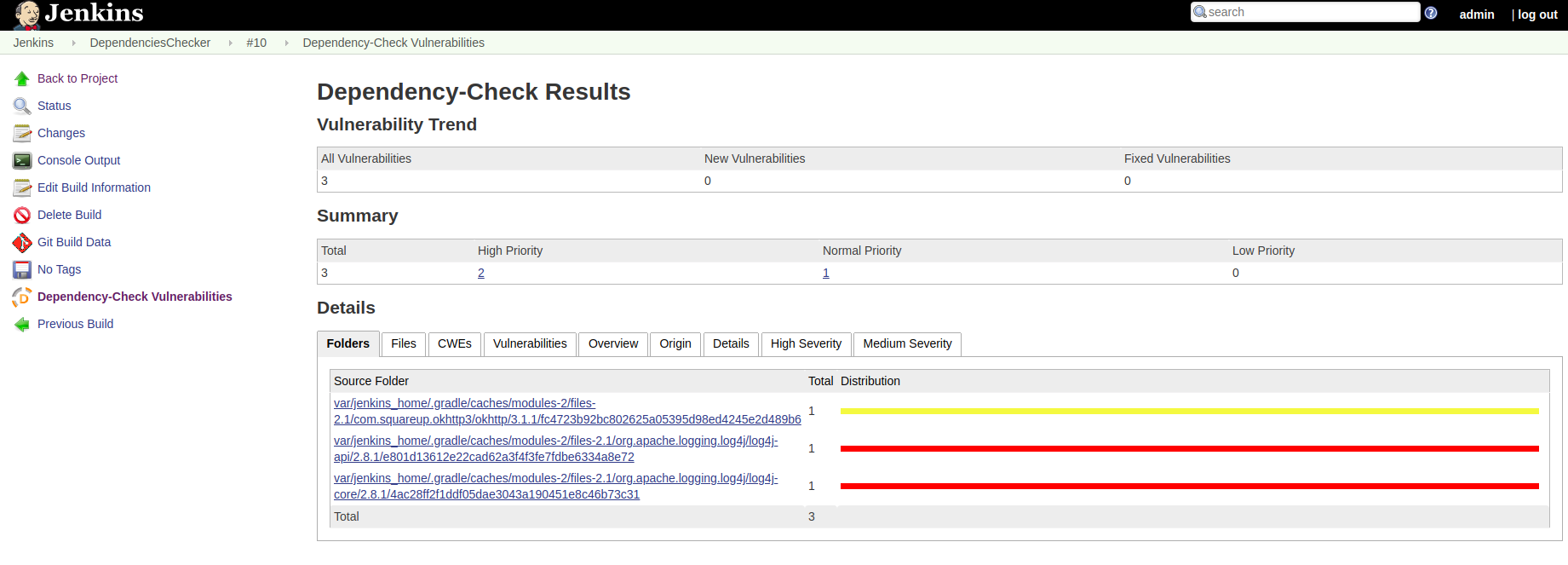
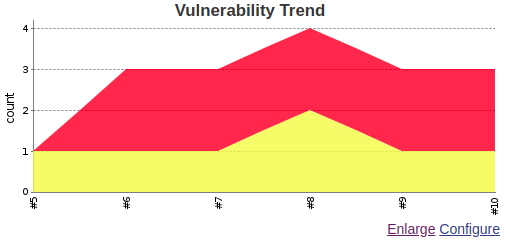
OWASP dependency check gradle plugin tasks
As saw previously, the Gradle task named dependencyCheckAnalyze allows to analyze your project. The first time, that your project is analyzed, the plugin needs to download and process the database of vulnerabilities from the NVD website. This step can be quite long, dependending on your internet connexion, your computer and so on.
If the time to update the database becomes a problem, one way to fix it, is to update your build.gradle to realize only the analysis without updating the database by setting autoUpdate=false and by setting the data directory to hold SQL CVEs contents with the following configuration:
|
|
With this configuration, it is your reponsibility to maintain and update the database of vulnerabilities. It can be done by using a script or another jenkins job that can be periodically executed to update your NVD data. To accomplish the update, there is a Gradle task named dependencyCheckUpdate.